
CMMC Compliance: Securing Your Future in Defense Contracting
Mastering CMMC: Your Ally in Navigating Cybersecurity Certification. With our guidance, the path to Cybersecurity Maturity Model Certification becomes clear and manageable, as we expertly steer you through the CMMC compliance landscape.
Understanding CMMC: Assessing Your Compliance Need
What is CMMC?
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard for implementing cybersecurity across the Defense Industrial Base (DIB), which includes over 300,000 companies in the supply chain. CMMC is designed to protect sensitive defense information housed on contractors’ information systems from cyber-attacks. It encompasses a range of cybersecurity standards and best practices, with the goal of enhancing the protection of Federal Contract Information (FCI) and, especially, Controlled Unclassified Information (CUI) within the supply chain.
Does my organization need to be CMMC compliant?
Any organization that handles FCI and/or CUI for the Department of Defense (DoD) is required to be CMMC compliant according to Federal Acquisition Regulation (FAR) section 4.1901 and Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7021 which outlines the Cybersecurity Maturity Model Certification (CMMC) requirements for contractors. This includes direct contractors and subcontractors in the defense supply chain. CMMC compliance is crucial for businesses seeking to secure or maintain contracts with the DoD.
If you answer “yes” to any of the items below, your organization must pursue compliance and ultimately become certified.
Criteria for CMMC Compliance
Does your organization contract or subcontract with the Department of Defense (DoD)?
If your organization is a contractor or subcontractor working with the DoD, then CMMC compliance is essential. This includes any entity that is part of the defense supply chain, directly or indirectly.
If your organization provides products or services to the DoD that are considered COTS, then it may be exempt.
Does your organization create, receive, store, and/or process FCI or CUI?
Handling of Controlled Unclassified Information (CUI): Compliance becomes necessary if your organization processes, stores, or transmits CUI. CUI encompasses various types of information that are sensitive but not classified. If your operations involve CUI, CMMC requirements apply.
Level of Involvement in the Defense Supply Chain: The required level of CMMC compliance depends on your role in the supply chain. Different contracts may require different CMMC levels, ranging from basic cyber hygiene to advanced security protocols.
Future Contract Aspirations: For organizations aiming to engage in future contracts with the DoD, obtaining CMMC certification is a proactive step. It not only prepares you for upcoming opportunities but also demonstrates a commitment to cybersecurity.
Steps to Certification
In today’s digital landscape, cybersecurity is not just a necessity; it’s a mandate, especially for organizations collaborating with the Department of Defense (DoD). Navigating the complexities of the Cybersecurity Maturity Model Certification (CMMC) can be challenging, but you don’t have to face it alone. We are dedicated to guiding you through every step of the CMMC compliance process with expertise and precision. Our services are specifically tailored to meet the unique needs of your organization while ensuring adherence to the highest standards of cybersecurity.
1. NIST SP 800-171 Compliance
Expert-Led Compliance Process: We initiate our services by ensuring your organization’s compliance with NIST SP 800-171, which forms the bedrock of the CMMC framework. Our team, composed of seasoned cybersecurity experts, specializes in aligning your current systems and practices with these stringent standards. We don’t just check for compliance; we embed best practices into your operational fabric, setting a strong foundation for subsequent CMMC levels.
2. Gap Assessment
Comprehensive and Customized Gap Analysis: Our gap assessment is an in-depth, tailored process. We meticulously analyze your existing security protocols against the specific CMMC level requirements relevant to your organization. Our approach is not one-size-fits-all; we recognize the unique challenges and needs of each client, offering customized solutions to bridge any identified gaps. This approach ensures a thorough and accurate path to compliance.
3. Controls Implementation
Tailored Control Strategies: Upon identifying the gaps, our team works to develop and implement the necessary cybersecurity controls. We focus on creating bespoke solutions that address your specific needs while ensuring minimal disruption to your business operations. Our implementation strategy is not just about meeting standards; it’s about enhancing your cybersecurity posture in a way that integrates seamlessly with your organizational processes.
4. Readiness Assessment (RPO)
Targeted Preparation and Support: As a Registered Provider Organization (RPO), we go beyond mere assessments. We provide comprehensive advisory and implementation services to prepare your organization for the CMMC assessment. Our team guides you through every step, offering insights, support, and solutions tailored to your specific circumstances. We ensure that your journey to compliance is well-informed, organized, and free from unnecessary complexities.
5. Certification (C3PAO)
Facilitating Smooth Certification: The final step involves a Certified Third Party Assessment Organization (C3PAO) conducting the official CMMC assessment. Our role in this phase is crucial. We liaise closely with the C3PAO to facilitate a smooth and efficient certification process. Our extensive preparatory work aims to ensure that your organization is not just ready for assessment but is positioned for success, minimizing the likelihood of any surprises during the certification.
Breaking down the requirement
CMMC
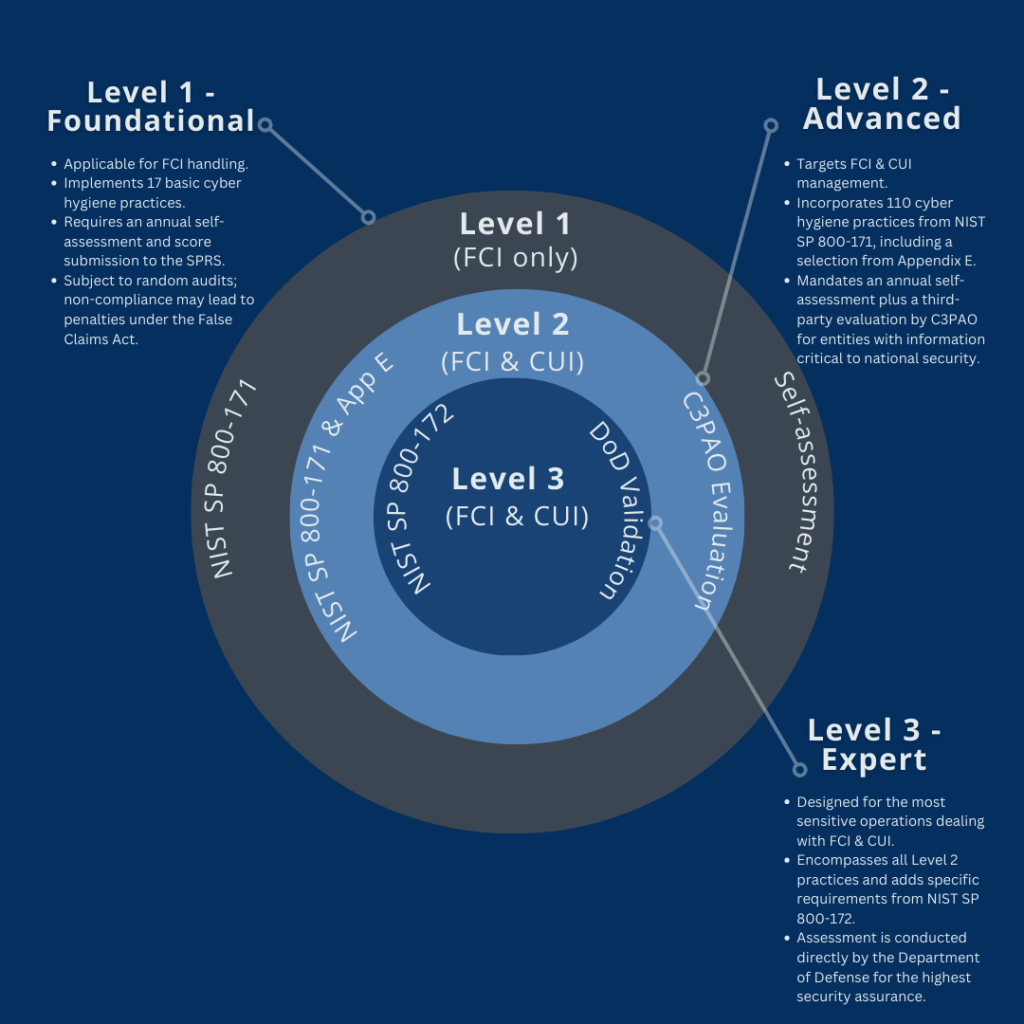
The CMMC framework consists of five cumulative levels of cybersecurity maturity, ranging from “Foundational” at Level 1 to “Expert at Level 3. Each level progressively builds on the previous one, with increasing sophistication in cybersecurity practices and processes. Organizations must meet the requirements and be certified at a specific level to be eligible for certain types of contracts.
DFARS 7012
Defense Federal Acquisition Regulation Supplement (DFARS) 7012 is a set of cybersecurity requirements that defense contractors must meet. It mandates that contractors provide adequate security to safeguard covered defense information on their networks and report cyber incidents. DFARS 7012 is closely tied to NIST SP 800-171 standards and serves as a precursor to CMMC.
NIST SP 800-171
The National Institute of Standards and Technology (NIST) Special Publication 800-171 provides guidelines on protecting CUI on non-federal systems and organizations. This standard is integral to DFARS 7012 compliance and forms the foundation for many CMMC practices and processes.
Why Choose A Training Program?
Instructor Expertise: Training programs in CMMC often feature instructors with extensive experience in the field. These professionals not only understand the CMMC framework thoroughly but also bring practical insights from their careers in cybersecurity and defense compliance. This real-world experience enriches the learning process, offering students a deeper understanding of how CMMC applies in various scenarios.
Comprehensive Course Content: A well-rounded CMMC training covers every facet of the model. This includes an exploration of the different levels and requirements of CMMC, as well as guidance on how to implement the necessary controls. The curriculum is designed to cater to both beginners and those seeking to expand their existing knowledge, providing a thorough grounding in all aspects of CMMC.
Practical Learning Approach: Emphasizing a hands-on experience, these courses often incorporate interactive sessions, case studies, and exercises. This approach ensures that learners can not only grasp theoretical concepts but also apply them in their organizational contexts. Such practical engagement is crucial for understanding and effectively implementing CMMC standards.
Flexible Learning Options: Recognizing the diverse needs and schedules of professionals, many CMMC training providers offer a variety of learning formats. Options may include in-person sessions, online courses, or a combination of both. This flexibility allows individuals to choose a learning method that best suits their personal and professional commitments.
Certification and Post-Training Support: Completing a CMMC training course typically results in a certificate, acknowledging the participant’s enhanced understanding and skills in CMMC assessment. Additionally, ongoing support from the training provider can be invaluable for integrating new knowledge into one’s organizational practices, ensuring a smooth transition and effective application of the CMMC framework.

Key Advantages of CMMC Education
✓ Expert Instruction
✓ Thorough Curriculum
✓ Hands-On Learning

Events
07/30/24 from 6:00-7:00 PM EST
CMMC Town Hall
We invite you to a special edition of the CMMC Town Hall during which we will be discussing CMMC updates and upgrades.
